Difference between revisions of "Securing OpenEMR"
From OpenEMR Project Wiki
(→XAMPP) |
m (→OpenEMR) |
||
| (34 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
=Securing OpenEMR= | =Securing OpenEMR= | ||
==Overview== | ==Overview== | ||
: | :Securing OpenEMR and your database requires a firm understanding of securing several parts, which at least include OpenEMR itself, Apache, MySQL, PHP, firewall, router, https, certficates, etc. A forum that began to discuss this issue can be [https://community.open-emr.org/t/onsite-or-offsite-patient-portal/2234 found here]. | ||
:There is also a very nice write up on [http://open-emr.org/wiki/index.php/Security_Assessment Security Assessment] for EMRs (especially regarding HIPAA compliance) on the wiki. | :There is also a very nice write up on [http://open-emr.org/wiki/index.php/Security_Assessment Security Assessment] for EMRs (especially regarding HIPAA compliance) on the wiki. | ||
:<span style="color:red;">'''This document is | :<span style="color:red;">'''This document is always a work in progress.'''</span> | ||
==OpenEMR== | ==OpenEMR== | ||
* | *After installation/upgrade, ensure you have installed most recent patch. | ||
*After installation/upgrade '''<span style="color:red;">remove the setup.php script</span>''', which is not needed for general OpenEMR use. | |||
*After installation/upgrade, '''<span style="color:red;">strongly recommend removing</span>''' (or ensuring no access to) to the following scripts, which are not needed for general OpenEMR use: | |||
*After installation/upgrade | |||
:*acl_setup.php | :*acl_setup.php | ||
:*acl_upgrade.php | :*acl_upgrade.php | ||
:*admin.php | :*admin.php | ||
:*sl_convert.php | :*sl_convert.php | ||
:* | :*sql_patch.php | ||
:*sql_upgrade.php | :*sql_upgrade.php | ||
:*gacl/setup.php | :*gacl/setup.php | ||
| Line 22: | Line 21: | ||
:*entire contrib directory | :*entire contrib directory | ||
::*(except for the contrib/icd9, contrib/icd10, contrib/snomed and contrib/rxnorm directories) | ::*(except for the contrib/icd9, contrib/icd10, contrib/snomed and contrib/rxnorm directories) | ||
:*entire Tests directory | :*entire tests directory (for versions prior to 5.0.1, this is the Tests directory) | ||
:*entire phpmyadmin directory | :*entire phpmyadmin directory (you do not need to do this for versions 5.0.1 and later, since phpmyadmin is not included in these versions) | ||
*After installing a patch, '''<span style="color:red;">strongly recommend removing</span>''' (or ensuring no access to) the following script, which is not needed for general OpenEMR use: | |||
*After installing a patch | |||
:*sql_patch.php | :*sql_patch.php | ||
*Settings (Adminstration->Globals in OpenEMR) | |||
:*Ensure [[Administration_Globals#Secure_Upload_Files_with_White_List|Secure Upload Files with White List]] setting is on. | |||
:*Ensure [[Administration_Globals#Enable_Encryption_of_Items_Stored_on_Drive|Enable Encryption of Items Stored on Drive]] setting is on. | |||
*Passwords | *Passwords | ||
:*Enforce strong/unique passwords, which can be set in Administration->Globals->Security. | :*Enforce strong/unique passwords, which can be set in Administration->Globals->Security. | ||
:*Enforce password expiration, which can be set in Administration->Globals->Security. | :*Enforce password expiration, which can be set in Administration->Globals->Security. | ||
*For OpenEMR versions 4.1.1 or less, remove the following file and directory, if they exist: | |||
:*FILE: library/openflashchart/php-ofc-library/ofc_upload_image.php | |||
:*DIRECTORY: library/openflashchart/tmp-upload-images/ | |||
*[https://www.open-emr.org/wiki/index.php/Multi-factor_Authentication Enable multi-factor authentication] | |||
==Network== | ==Network== | ||
| Line 36: | Line 41: | ||
==Apache== | ==Apache== | ||
*General hardening of Apache, which is [http://www.learncomputer.com/secure-apache/ described here], and here for [http://httpd.apache.org/docs/2.4/misc/security_tips.html apache2.4]. | *General hardening of Apache, which is [http://www.learncomputer.com/secure-apache/ described here], and here for [http://httpd.apache.org/docs/2.4/misc/security_tips.html apache2.4]. | ||
*Only allow https (ie. turn off http). It's pretty easy to setup for [https://www.digitalocean.com/community/tutorials/how-to-create-a-ssl-certificate-on-apache-for-ubuntu-14-04 Debian/Ubuntu]. | *Only allow https (ie. turn off http). It's pretty easy to setup for [https://www.digitalocean.com/community/tutorials/how-to-create-a-ssl-certificate-on-apache-for-ubuntu-14-04 Debian/Ubuntu]. | ||
*Do not allow direct web access to the following | *Do not allow direct web access to the following directory | ||
:*sites/*/documents | :*sites/*/documents | ||
*Do not allow use of .htaccess files in Apache (ie. turn off the AllowOverride setting). | *Do not allow use of .htaccess files in Apache (ie. turn off the AllowOverride setting). | ||
*If not using portal and want to allow users to access over the internet, then consider using client-sided certificates to only allow users access to site | *If not using portal and want to allow users to access over the internet, then consider using client-sided certificates to only allow users access to site | ||
| Line 47: | Line 50: | ||
*If want to give access to the onsite patient portal over the internet, then consider using a client-sided certificate to only allow users access to the main OpenEMR login page (this is not optimal, though). | *If want to give access to the onsite patient portal over the internet, then consider using a client-sided certificate to only allow users access to the main OpenEMR login page (this is not optimal, though). | ||
==MySQL== | ==MySQL/MariaDB== | ||
*Ensure the root password is set to something. | *Ensure the root password is set to something. Pick a hard password; one that includes capital letters, lowercase letters, numbers, and symbols. | ||
*Do the same for the openemr user and give it privileges only to the openemr database. | |||
*If you are using PHPMyAdmin be sure to use two-factor authentication. | |||
==PHP== | ==PHP== | ||
| Line 58: | Line 63: | ||
*for newer versions of XAMPP please see this: | *for newer versions of XAMPP please see this: | ||
Information on setting a root password for the database can be found in the "HOW-TO Guides" for XAMPP for windows version 5.6.20 (enter localhost in browser). | |||
*for older versions (~pre 2016) Navigate to the Security Console via http://localhost/security/xamppsecurity.php in the URL address bar. | *for older versions (~pre 2016) Navigate to the Security Console via http://localhost/security/xamppsecurity.php in the URL address bar. | ||
| Line 86: | Line 91: | ||
*Navigate to the Status section from the left sidebar. If there are 3 green "Secure" bars, this exercise has been successful. | *Navigate to the Status section from the left sidebar. If there are 3 green "Secure" bars, this exercise has been successful. | ||
[[File:Secure2.png|center]] | [[File:Secure2.png|center]] | ||
==Nginx and PHP-FPM== | |||
Check out this article which includes ssl files for securing openemr: | |||
::[https://www.open-emr.org/wiki/index.php/OpenEMR_with_nginx_and_php-fpm OpenEMR with Nginx and PHP-FPM] | |||
Here is a very nice write up on security for Linux systems: | |||
::[https://www.cyberciti.biz/tips/linux-unix-bsd-nginx-webserver-security.html Top 25 Nginx Web Server Best Security Practices] | |||
==Codebase== | ==Codebase== | ||
*[[Codebase_Security|Ongoing project to | *[[Codebase_Security|Ongoing project to maintain security of the codebase.]] | ||
*Consider adding a specific sqlconf.php override settings when using the patient portal (especially the onsite portal), which can be used to use a separate mysql user (and possibly database). | *Consider adding a specific sqlconf.php override settings when using the patient portal (especially the onsite portal), which can be used to use a separate mysql user (and possibly database). | ||
<br> | <br> | ||
Latest revision as of 04:50, 25 January 2023
Securing OpenEMR
Overview
- Securing OpenEMR and your database requires a firm understanding of securing several parts, which at least include OpenEMR itself, Apache, MySQL, PHP, firewall, router, https, certficates, etc. A forum that began to discuss this issue can be found here.
- There is also a very nice write up on Security Assessment for EMRs (especially regarding HIPAA compliance) on the wiki.
- This document is always a work in progress.
OpenEMR
- After installation/upgrade, ensure you have installed most recent patch.
- After installation/upgrade remove the setup.php script, which is not needed for general OpenEMR use.
- After installation/upgrade, strongly recommend removing (or ensuring no access to) to the following scripts, which are not needed for general OpenEMR use:
- acl_setup.php
- acl_upgrade.php
- admin.php
- sl_convert.php
- sql_patch.php
- sql_upgrade.php
- gacl/setup.php
- ippf_upgrade.php
- entire contrib directory
- (except for the contrib/icd9, contrib/icd10, contrib/snomed and contrib/rxnorm directories)
- entire tests directory (for versions prior to 5.0.1, this is the Tests directory)
- entire phpmyadmin directory (you do not need to do this for versions 5.0.1 and later, since phpmyadmin is not included in these versions)
- After installing a patch, strongly recommend removing (or ensuring no access to) the following script, which is not needed for general OpenEMR use:
- sql_patch.php
- Settings (Adminstration->Globals in OpenEMR)
- Ensure Secure Upload Files with White List setting is on.
- Ensure Enable Encryption of Items Stored on Drive setting is on.
- Passwords
- Enforce strong/unique passwords, which can be set in Administration->Globals->Security.
- Enforce password expiration, which can be set in Administration->Globals->Security.
- For OpenEMR versions 4.1.1 or less, remove the following file and directory, if they exist:
- FILE: library/openflashchart/php-ofc-library/ofc_upload_image.php
- DIRECTORY: library/openflashchart/tmp-upload-images/
Network
- On server, consider only opening port 443 (https).
- Consider a firewall that only allows port 443 (https) traffic to the server.
Apache
- General hardening of Apache, which is described here, and here for apache2.4.
- Only allow https (ie. turn off http). It's pretty easy to setup for Debian/Ubuntu.
- Do not allow direct web access to the following directory
- sites/*/documents
- Do not allow use of .htaccess files in Apache (ie. turn off the AllowOverride setting).
- If not using portal and want to allow users to access over the internet, then consider using client-sided certificates to only allow users access to site
- If using third party patient portal, then use the current method whereby your instance is not on the internet and connects to the third party patient portal via vpn.
- If want to give access to the onsite patient portal over the internet, then consider using a client-sided certificate to only allow users access to the main OpenEMR login page (this is not optimal, though).
MySQL/MariaDB
- Ensure the root password is set to something. Pick a hard password; one that includes capital letters, lowercase letters, numbers, and symbols.
- Do the same for the openemr user and give it privileges only to the openemr database.
- If you are using PHPMyAdmin be sure to use two-factor authentication.
PHP
- Use a Supported Version of PHP.
- Follow the OpenEMR php settings recommendations
XAMPP
- If you are using XAMPP, note that this software is extremely unsecure after installation and you need to secure it by configuring the Security Console.
- for newer versions of XAMPP please see this:
Information on setting a root password for the database can be found in the "HOW-TO Guides" for XAMPP for windows version 5.6.20 (enter localhost in browser).
- for older versions (~pre 2016) Navigate to the Security Console via http://localhost/security/xamppsecurity.php in the URL address bar.
- If the Welcome page is in German, it can be changed in the left sidebar, under Sprachen. Language selection can also be accomplished from the splash page or in the upper right hand corner of a webpage.
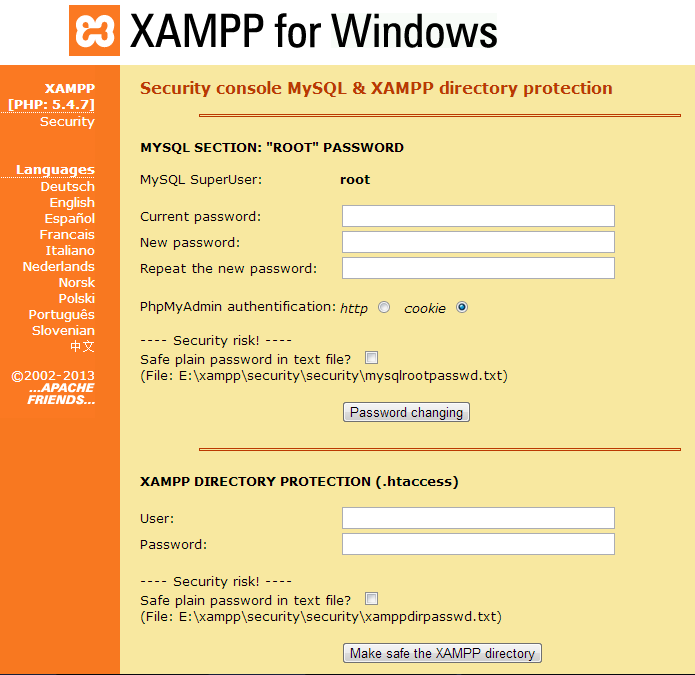
- Navigate to the Security section.
- The first task is to set the MySQL root password. The question under "Security Risk!" asks if you wish to store the password in plain text. The first word is a verb, not an adjective; "save" instead of "safe". Users who are apt to losing things may wish to choose this option despite an increased risk. Click "Password Changing" button to save.
- The second task is to set the password to the Security Console. Click "Make safe the XAMPP directory" button to save.
- If this password is lost and not saved in plain text, it would be very difficult to gain access to the Security Console to change the MySQL root password. Knowing the MySQL root password allows the user to import the database to a new device or installation of OpenEMR at some future time.
- If the user needs to gain access to phpMyAdmin externally (outside of OpenEMR), he must know the MySQL root password.
- If the user opts to save the passwords in plain text, the paths to the folders containing the passwords are given.
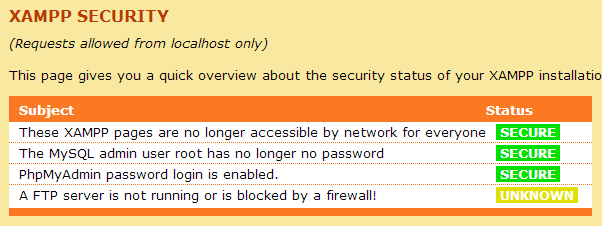
- Navigate to the Status section from the left sidebar. If there are 3 green "Secure" bars, this exercise has been successful.
Nginx and PHP-FPM
Check out this article which includes ssl files for securing openemr:
Here is a very nice write up on security for Linux systems:
Codebase
- Ongoing project to maintain security of the codebase.
- Consider adding a specific sqlconf.php override settings when using the patient portal (especially the onsite portal), which can be used to use a separate mysql user (and possibly database).
Security Assessment
- A security risk assessment is a requirement in the US for compliance with HIPAA and Meaningful Use. There is a very nice write up on this topic on the Security Assessment wiki page.