Difference between revisions of "Auditable events and tamper-resistance (MU3)"
From OpenEMR Project Wiki
Bradymiller (talk | contribs) |
(→Notes) |
||
| (36 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
: | ==Status== | ||
:*'''VERIFIED COMPLETE''' | |||
:*Ready to sign self-declaration. | |||
:*To ensure accurate time, server will need to set up a Network Time Protocol server that supports Network Time Protocol (NTP) | ==Notes== | ||
[[File:D2.png|1000px|border|link=]] | |||
<br> | |||
<br> | |||
<br> | |||
:Issues: | |||
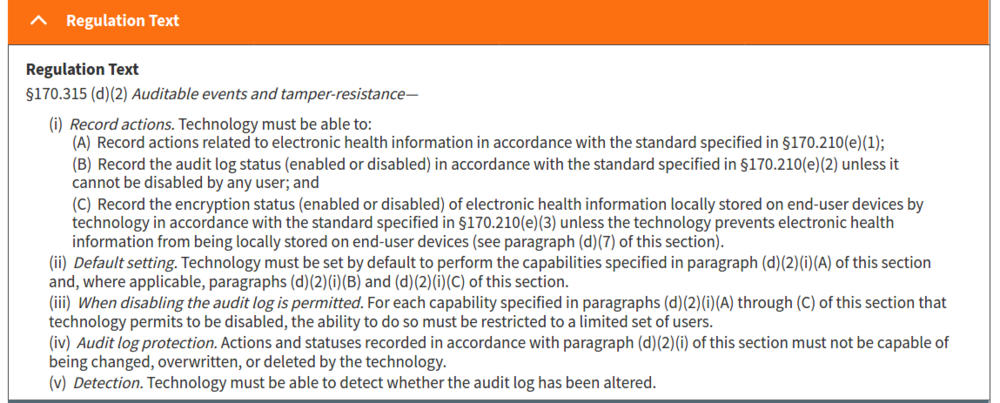
:(d)(2)(i)(A) | |||
::*The audit log must record the information specified in sections 7.1.1 through 7.1.3 and 7.1.6 through 7.1.9 of the standard specified in ASTM E2147-18 and changes to user privileges when health IT is in use. ('''PASS''') | |||
:::*CLARIFICATION | |||
::::*Support for 7.1.3 (Duration of access) was dropped since was not felt to be in scope for certifying and testing to ONC certification. | |||
:(d)(2)(i)(B) | |||
::*The audit log must record the information specified in sections 7.2 and 7.4 of the standard specified in ASTM E2147-18 when the audit log status is changed. Interestingly, 7.2 and 7.4 do not exist in ASTM E2147-18, but in a prior ASTM E2147-01 version used in MU2, 7.2 was 'Date and Time of Event' and 7.4 was 'User Identification'; notably there was a clarification to fix this and need to support 7.1.1 (Date and Time of access event) and 7.1.7 (User Identification). ('''PASS''') | |||
:(d)(2)(i)(C) | |||
::*End-user device encryption is always on per (d)(7), so not applicable. ('''PASS''') | |||
:(d)(2)(ii) | |||
::*All logging needs to be on by default. ('''PASS''') | |||
:(d)(2)(iii) | |||
::*Logging can only be disabled by a limited set of users. ('''PASS''') | |||
:(d)(2))(iv) | |||
::*Can not manipulate (changed, overwritten, or deleted) log. ('''PASS''') | |||
:(d)(2))(v) | |||
::*Need to detect manipulation of log. ('''PASS''') | |||
:Final: | |||
:*To ensure accurate time, server will need to set up a Network Time Protocol server that supports version 4 Network Time Protocol (NTP) as defined by RFC 5905. | |||
Latest revision as of 20:36, 7 June 2024
Status
- VERIFIED COMPLETE
- Ready to sign self-declaration.
Notes
- Issues:
- (d)(2)(i)(A)
- The audit log must record the information specified in sections 7.1.1 through 7.1.3 and 7.1.6 through 7.1.9 of the standard specified in ASTM E2147-18 and changes to user privileges when health IT is in use. (PASS)
- CLARIFICATION
- Support for 7.1.3 (Duration of access) was dropped since was not felt to be in scope for certifying and testing to ONC certification.
- (d)(2)(i)(B)
- The audit log must record the information specified in sections 7.2 and 7.4 of the standard specified in ASTM E2147-18 when the audit log status is changed. Interestingly, 7.2 and 7.4 do not exist in ASTM E2147-18, but in a prior ASTM E2147-01 version used in MU2, 7.2 was 'Date and Time of Event' and 7.4 was 'User Identification'; notably there was a clarification to fix this and need to support 7.1.1 (Date and Time of access event) and 7.1.7 (User Identification). (PASS)
- (d)(2)(i)(C)
- End-user device encryption is always on per (d)(7), so not applicable. (PASS)
- (d)(2)(ii)
- All logging needs to be on by default. (PASS)
- (d)(2)(iii)
- Logging can only be disabled by a limited set of users. (PASS)
- (d)(2))(iv)
- Can not manipulate (changed, overwritten, or deleted) log. (PASS)
- (d)(2))(v)
- Need to detect manipulation of log. (PASS)
- Final:
- To ensure accurate time, server will need to set up a Network Time Protocol server that supports version 4 Network Time Protocol (NTP) as defined by RFC 5905.